February 1, 2025• byEric L.

Online Banking • Phishing • Scams • Security
January 28, 2025• byEric L.
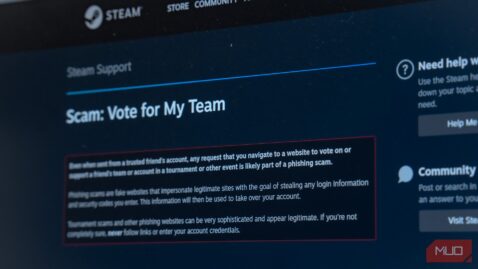
Cybersecurity • Data Security • Phishing • Security • steam
January 18, 2025• byEric L.
November 23, 2024• byJeremy P.
CES® is the registered trademark of The Consumer Technology Association.® CBMG is not endorsed by, affiliated with, or sponsored by CES.