
Your phone holds more sensitive data than your wallet, diary, and filing cabinet combined. Banking details, private messages, health records, and location history travel with you everywhere. Cybercriminals know this goldmine exists in your pocket. The good news? You don’t need a computer science degree to protect yourself. These 22 security moves will fortify your device without breaking your brain or budget.
22. Restart Your Phone Weekly

Rebooting disrupts memory-resident malware and kicks out unauthorized processes lurking in your system. The NSA and security experts recommend weekly restarts for both iPhone and Android devices. This simple habit removes temporary system modifications that hackers exploit through zero-click attacks. Your phone gets a fresh start while malware gets the boot. Set a weekly reminder and treat it like basic maintenance that prevents bigger headaches.
Pro tip: Schedule your restart for Sunday nights when you’re likely at home and can afford the brief downtime. Hold the power button and volume up (iPhone) or power button (Android) to restart properly.
21. Enable Two-Factor Authentication

Microsoft and Google research confirms that 2FA blocks 99.9% of automated attacks, even when passwords get compromised. The extra verification step creates a roadblock that frustrates cybercriminals targeting your cloud accounts. Authentication apps or SMS codes add minimal friction while delivering massive protection benefits. That extra 10 seconds during login saves hours of damage control later when accounts stay secure.
20. Use a VPN on Public Wi-Fi

Public networks lack encryption that protects your data from interception by nearby attackers. Security experts strongly recommend VPN usage on public Wi-Fi to encrypt traffic and prevent eavesdropping. Hackers can monitor unprotected connections to steal passwords, credit card details, and personal messages in real-time. Choose a reliable VPN service and activate it before connecting to any untrusted network.
19. Turn Off Developer Mode
Developer Mode unlocks advanced functions that create massive security risks for everyday users. Security researchers link this feature to increased vulnerability, especially when USB debugging stays active. The extra access opens doors for exploit installation and unauthorized system changes. Most smartphone users can eliminate this attack vector by simply disabling Developer Mode in their settings. Check your device and turn it off if you’re not actively developing apps.
How to check: Android users go to Settings > About Phone and tap “Build Number” 7 times to reveal developer options, then disable them. iPhone users won’t have this unless they’ve specifically enabled development tools.
18. Monitor App Privacy Reports
App Privacy Report reveals which applications access your camera, microphone, location, and contact data along with frequency statistics. The iOS 15+ feature provides transparency about app behavior that helps identify suspicious data collection patterns. Review reports regularly to spot applications accessing more information than necessary for their stated functionality. Remove apps that demonstrate excessive data hunger compared to their actual feature requirements.
17. Avoid Jailbreaking or Rooting

Jailbreaking strips away built-in security protections and disables critical sandboxing features. Security firms like ESET document how these modifications expose devices to malware that bypasses normal defenses. The customization benefits don’t justify the massive security risks you’re accepting. Stick with your phone’s stock operating system, which includes layers of protection designed to keep threats out of your personal data.
16. Check for Unknown Device Profiles
Hidden device management profiles can monitor activity and compromise privacy without user knowledge or consent. These configurations often install through malicious apps or compromised network connections according to security resources. Open Settings, then General, then VPN & Device Management to review all installed profiles. Remove any profiles you don’t recognize immediately, as personal devices should remain under your complete administrative control.
15. Clear Safari History Regularly
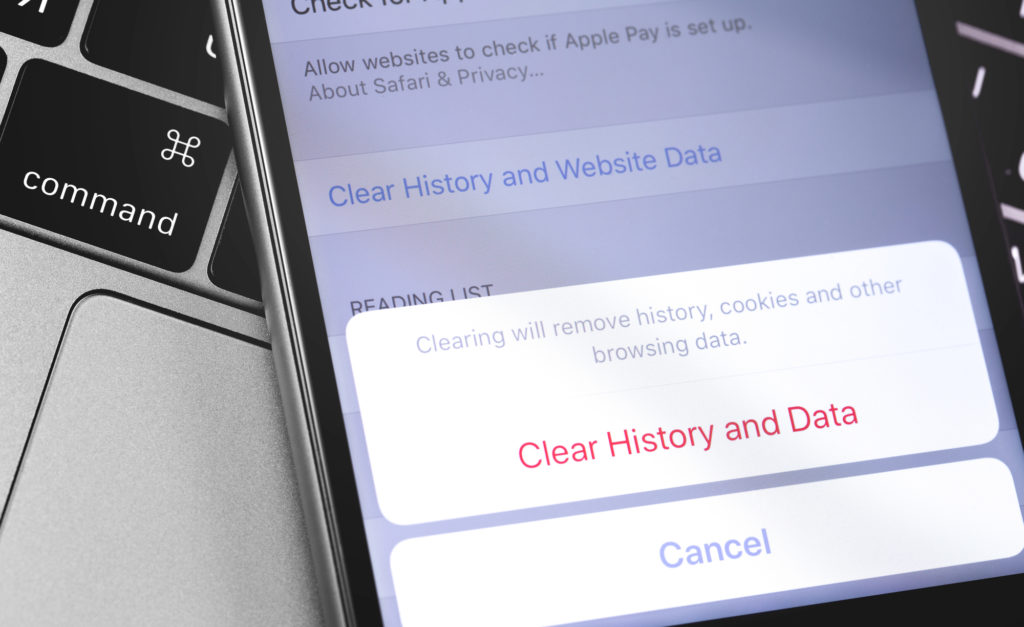
Regular history clearing removes tracking cookies and cached data that companies use to build detailed user profiles. Navigate to Settings, then Safari, then “Clear History and Website Data” to remove accumulated tracking information. Apple guidance recommends this practice for iOS users concerned about online privacy and behavioral advertising. Frequent cleaning prevents websites from correlating your browsing patterns across extended time periods.
14. Install a Reputable Security App

Malware threats continue growing at alarming rates, making security apps essential protection for mobile devices. Established options like Bitdefender, Norton, and McAfee offer real-time scanning and anti-phishing features. Run regular system scans and keep security definitions updated automatically for maximum effectiveness. Premium versions provide additional features like VPN access and identity monitoring that justify the monthly cost.
13. Set Up Automatic Security Updates
Manual update checking creates dangerous security gaps that attackers exploit between patch releases and user installation. Apple expanded their Rapid Security Response program in 2023, delivering critical fixes faster than traditional update cycles. Navigate to Settings, then General, then Software Update to enable automatic installation of security patches. Your device receives protection against the latest threats without waiting for manual intervention or approval.
12. Configure Lock Screen Access

Lock screen convenience features can expose sensitive information to unauthorized users who gain physical device access. Apple documentation explains how to disable Control Center, Siri, and Wallet access when your device remains locked. Review notification settings to prevent private message content from appearing on the lock screen display. Balance accessibility with security based on your personal risk tolerance and usage patterns.
11. Turn On Google Play Protect (Android)

Google Play Protect provides built-in security scanning for Android devices around the clock. Open the Google Play Store, tap your profile, then select “Play Protect” to verify activation status. Enable both app scanning and harmful app detection for comprehensive coverage of new downloads and existing applications. The system monitors installed software continuously for suspicious behavior patterns without requiring user intervention.
10. Use a Strong Passcode or Biometric Lock

Weak passcodes offer zero protection against determined attackers. Security organizations recommend passwords with at least 8 characters including mixed case letters, numbers, and symbols. Biometric authentication adds convenience while maintaining strong security standards. Fingerprint and facial recognition technology continues improving, making these options increasingly reliable for daily use. Your lock screen serves as the first barrier between thieves and your personal data.
Smart choices: Use 6-digit passcodes minimum on iPhone, avoid patterns on Android. Set up multiple fingerprints (index and thumb) for easier unlocking. Enable “Erase Data” after 10 failed attempts for ultimate protection.
9. Verify Personal Recovery Information
Outdated recovery information creates account lockout situations that security experts see regularly in support cases. Review contact details quarterly to ensure accuracy in your account recovery settings across all platforms. Verify that backup email addresses and phone numbers remain accessible and under your control. Update personal information when anything changes to maintain account access during password reset or compromise situations.
8. Connect Only to Secure Wi-Fi Networks

Unsecured networks broadcast your data without encryption protection that prevents eavesdropping by nearby attackers. Look for lock icons next to network names before connecting to verify that proper security measures are active. Use mobile data or create personal hotspots instead of risking exposure on public networks. When public Wi-Fi becomes necessary, activate VPN protection immediately to encrypt your connection tunnel.
7. Enable Lockdown Mode (iOS)

Lockdown Mode severely limits your device’s attack surface during suspected targeted attacks. Apple designed this feature to block advanced spyware by restricting high-risk functions and website capabilities. Website browsing becomes limited and message previews disappear, but sophisticated attackers hit significant barriers. Activate this mode if you work in high-risk industries or suspect targeted surveillance attempts against your device.
6. Download Apps from Trusted Sources Only

Official app stores maintain screening processes that reduce malware distribution compared to unofficial sources. Google Play and Apple’s App Store implement security measures that catch most malicious software before it reaches users. Third-party app stores pose higher malware risks according to security researchers. Read reviews before downloading and avoid apps requesting excessive permissions that don’t match their stated function.
5. Keep Your Operating System Updated
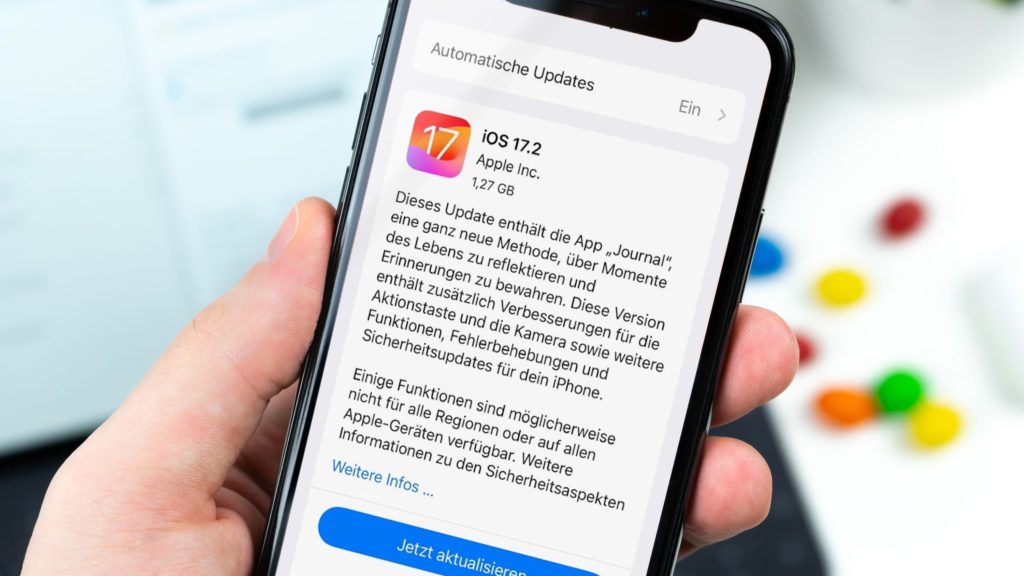
Security patches fix vulnerabilities faster than hackers can exploit them. Cybersecurity experts confirm that delayed updates create welcome mats for cybercriminals targeting outdated systems. Enable automatic updates to receive continuous protection without lifting a finger. Your device downloads and installs critical fixes while you sleep, blocking common malware before it reaches your data. Missing updates increases your risk exponentially.
Quick setup: iPhone users go to Settings > General > Software Update > Automatic Updates. Android users navigate to Settings > System > System Update > Auto-download over Wi-Fi.
4. Spot and Block Scam Messages

Cybersecurity agencies report that scam messages use pressure tactics and urgency to trick users into clicking malicious links. Watch for telltale signs like spelling errors, generic greetings, and demands for immediate action on account security. Legitimate companies rarely send urgent alerts through unsolicited text messages about compromised accounts. Delete suspicious messages immediately and block senders to prevent future social engineering attempts.
3. Change Your Apple Account Password
Apple accounts control access to photos, messages, location data, and payment information stored in iCloud. Security experts recommend passwords with at least 8 mixed characters that avoid predictable patterns like birthdays or dictionary words. Password managers generate and store complex credentials safely while eliminating reuse across multiple accounts. Navigate to Settings, tap your name, then Password & Security to update credentials on a regular schedule.
2. Enable Private Relay (iOS)
Private Relay routes Safari traffic through Apple servers to obscure your IP address from websites and limit tracking capabilities. Navigate to Settings, tap your name, then iCloud to locate Private Relay configuration options. The service reduces targeted advertising effectiveness while protecting browsing privacy from data collection companies. Note that Private Relay only functions in Safari browser, not other applications or browsing alternatives.
1. Activate Stolen Device Protection

Stolen Device Protection requires biometric authentication plus time delays for security-sensitive changes when away from familiar locations. Face ID or Touch ID verification combines with one-hour waiting periods for critical account modifications. Password changes and payment method updates become significantly harder for thieves to execute quickly. Early reports suggest this protection reduces successful identity theft following device theft incidents.
Last modified: August 20, 2025







